
How to Prevent Zoom Bombing
Have you been zoom bombed before? In this article, you will learn what is zoom bombing and how to prevent zoom bombing, zoom bomb, zoom bombs, zoom bomber or zoom bombings and secure your meetings.
When the coronavirus spread, consumers and organizations switched to video conversations, one of which being Zoom meetings.
A fraction of the millions of Zoom call participants are trolls whose purpose is to disrupt or distract Zoom calls with upsetting or distracting information.
These Zoom bombers may utilize nudity, use threatening language, or share other graphic pictures to disrupt meetings. To add to the worry, security experts discovered that the bulk of Zoom bombing attacks target high school and college students.
According to accounts, the “Zoom bombing” has a significant impact on a large number of individuals. Every day, several occurrences occur, generating extremely unpleasant working circumstances. As a result of the numerous leaks of zoom video conversations, several calls were bombed and forced to end quicker.
Let’s examine what you can do to avoid this happening during your meeting.
Table of Contents
What is Zoom bombing?
Zoom bombing meaning: The entry of strangers or online trolls into a Zoom or video conference session is known as zoom bombing.
The purpose of a Zoom bomber is to cause mayhem in the meeting in a number of ways, most commonly by introducing pornographic photographs or other distracting content.
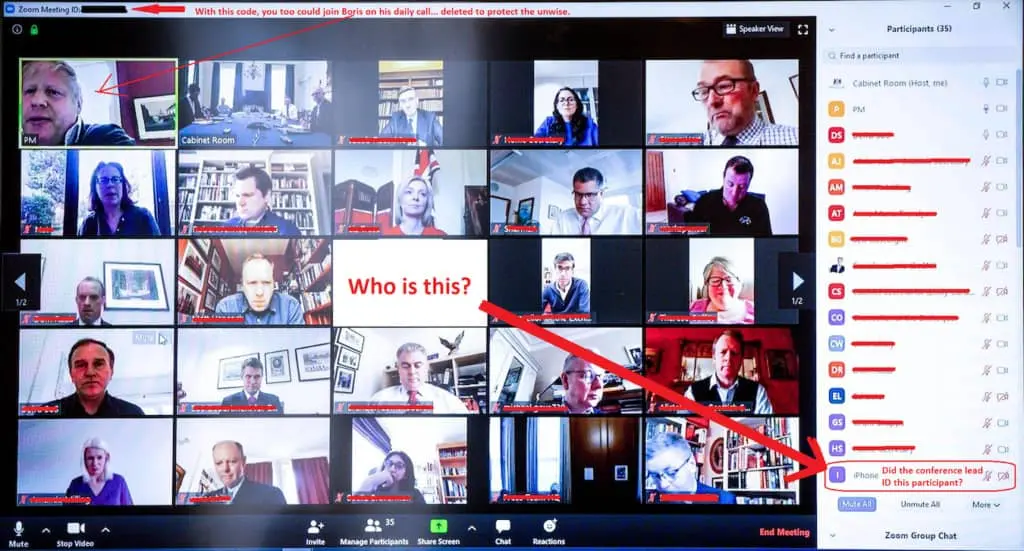
Uninvited visitors frequently share their screens after they obtain access to a meeting in order to take control of the conference and bombard members with distracting or unlawful information.
Some individuals believe that zoom — is secure and may be used to communicate sensitive business information. If hackers get their hands on this information, it may be disastrous for business.
Is zoom bombing a crime
Because of the increasing frequency of these instances, federal officials, the Department of Justice, and US Attorneys’ offices have declared Zoom bombing to be an unlawful and potentially federal violation.
Individuals engaging in these activities might face federal and state charges, according to a severe warning placed on the Department of Justice’s website under the U.S. Attorney’s office in 2020. Fines and possibly jail are possible outcomes.
Zoom bombing charges may include the following acts, according to law enforcement officials:
- Disruption of a public meeting
- Computer intrusion
- Using a computer to commit a crime
- Spreading hate crimes
- Committing fraud
- Transmission of threatening communications
Is zoom bombing still happening
While anybody may be the victim of a Zoom bombing, there are things you can do to lessen your chances of being targeted.
Zoom has released new security features that you may customize while on a call, and you can also protect your conference ahead of time by disabling and activating the appropriate settings.
How do hackers zoom bomb without any permission to join
The majority of the hackers did not exploit any vulnerabilities in the code or hacking software. It all boils down to zoom’s privacy settings.
If you create a public meeting, anybody with the link can attend. Trolls usually discover these URLs on the internet; occasionally authors publish them, and sometimes others leak Zoom meeting links. Big platforms like Twitter and Reddit are currently attempting to prohibit related posts.
How to prevent zoom bombing and secure your meetings
Let’s go through some of the most critical things you can do to protect yourself, and you can also read about privacy in zoom on their official site.
1. Never publicize your meeting URLs
First and foremost, never disclose your meeting URLs on Twitter, Facebook, or any other social media platform; it’s a simple step. It is preferable to distribute links via other means, such as email or a customized bot that will send each participant a private message.
2. Set your meeting to private mode
The second step is to make sure that your meeting is set to private mode, which requires others to enter your video conference using a link and password. Although Zoom now makes all meetings private by default, if you do not establish a new group every time, you just need to check this parameter.
3. Calls should have a unique ID
Your personal ID is never shared with anyone in the third part. It’s a unique meeting ID that you receive when you create a Zoom account. It’s significant since it never changes and you can’t modify it, so sharing it anyplace might cause serious difficulties.
Hackers will use your ID to detonate bombs at other events. This ID should only be shared with trustworthy and secure individuals; unfortunately, it is required for quick, one-time encounters.
When you realize that your ID has been stolen or that you have disclosed it in public, you must contact Zoom Support to get it changed.
4. Set screen sharing controls
Fourth, whether you’re giving a presentation or giving a lecture, ensure sure screen-sharing is set to host only.
Before the meeting, set up screen sharing controls as follows:
- Go to the Zoom web portal (not the desktop app) and navigate to Personal > Settings > In Meeting (Basic) and look for “Screen sharing.”
- Select the option “Only Host.”
To control screen sharing during a meeting, follow these steps:
- Navigate to the host controls (these will be viewable from your screen if you’re the host) and click the arrow next to Screen Share.
- Select “Advanced Sharing Options.”
- Under “Who can share?” select the option “Only Host.”
What to do if your zoom meeting is hacked
If a Zoom bomber interrupts your conference, you may take several measures in addition to removing them from the meeting.
1. Report the intruder to Zoom
If you come across a Zoom bomber, report it to Zoom while the meeting is still going on, if possible. If you can submit the report while the meeting is still in progress, the host can choose which participants to report and forward it to the Zoom Trust & Safety team for additional review.
2. Remove the intruder from your meeting
Click “Participants” from the host controls while the meeting is in progress, then mouse over the name of the individual you wish to remove and select “Remove.”
3. Review the Zoom settings
Examine the Zoom settings listed above to make sure yours are set to the appropriate security levels.
Is zoom safe for video call?
You can guard against a Zoom bombing assault and keep attackers at bay by following the security procedures outlined above. Equipping yourself with a cross-platform antivirus that protects all of your devices is a wonderful approach to better safeguard your network and protect yourself and your data.
As you can see after going through all of these stages, zoom is truly safe because there are no large holes in the code or issues with unsafe connections.
Zoom programmers go to great lengths to make their software secure and simple to use. Essentially, all difficulties stem from the human component; simply follow these simple instructions, and Zoom will be a very safe location to conduct corporate meetings, private video calls, or lectures.
FAQ
Why do people zoom bomb
A Zoom bomber’s goal is to wreak havoc in a variety of ways, most often by inserting obscene images or other distracting content into the meeting.
Is zoom bombing still happening
Zoom-bombing incidents, which can be very offensive and disruptive, are still happening across many institutions. Zoom offers multiple security features to protect your meetings.
Is zoom-bombing illegal
According to the Computer Fraud and Abuse Act, it is a criminal offense to access computers without authorization. In the same sense, accessing a video meeting that you do not have authorization for makes Zoombombing illegal as well. It is considered a cyber-crime, and any victim of a teleconference hijacking can report it as an incident.
How to handle zoom bombing
- Use a Unique ID for Calls. Every Zoom user has a Personal Meeting ID (PMI) that functions similarly to a phone number.
- Always Set a Meeting Password.
- Use the Waiting Room Feature.
- Set Screen Sharing Controls.
- Lock Your Meeting.
- Disable Users’ Audio and Video.
- Remove Users from Meetings.
